
BrainSploit - The InfoSec Blog
Welcome to my blog. Writing a blog about audits would be toooo boring. Therefore, I share some thoughts about exploits, offensive security matters and hacking stuff. Please feel free to share your comments.
Filter Categories
-

-

The Hard Way of Emulating Firmware Part 2
-

The Hard Way of Emulating Firmware Part 1
-
Exploiting Path Traversal - The Creative Way
-
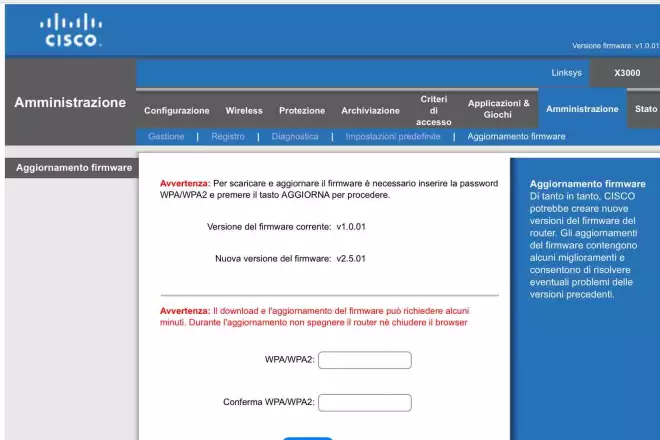
Create an evil twin to phish wifi keys
-
Sniff Wifi Traffic to uncover Secrets of your Home Devices - Part 1
-

Sniff Wifi Traffic to uncover Secrets of your Home Devices - Part 2
-
Get interesting data by sniffing SNMP traffic
-

Create a rogue access point with a Linux VM
-
Exploit and Detect Pan OS < 11.1 Command Injection
-
Exploiting Boa Webserver 0.94.14rc21 Path Traversal
-
Testing Log4J Remote Code Execution
-
How JSON web tokens work
-
Exploiting Buffer Overflows - a real world example
-
How to exploit JSON web tokens
-
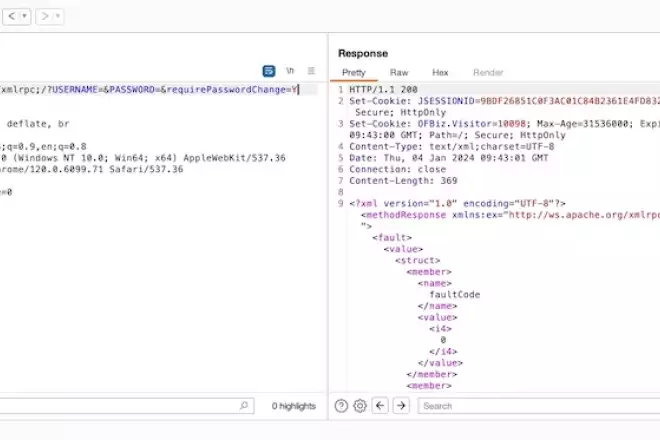
How to test and exploit Apache Ofbiz < 18.12.10. Authentication Bypass & Command Injection
-
Understanding and testing Buffer Overflows
-
How the Stack works